“Software service agreements” are important legal documents which regulate the use of software, licensing, intellectual property rights, rights and responsibilities of the parties, and often prevent disputes or serve as legal basis in litigation. As part of the Software Service Agreement, the
Read More
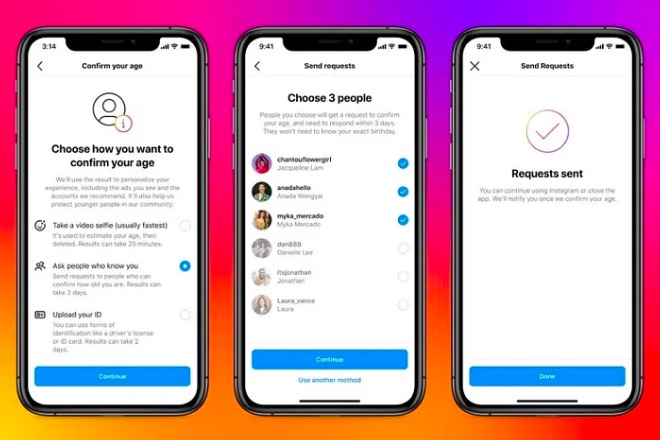
Meta announced that Instagram have started to perform age verification through US citizen users video analytics with the support of 3rd party companies in order to protect children from unwanted/illicit content. Thus, we will see examples of deep learning and age algorithm
Read More
The Federal Bureau of Investigation (FBI) warns that employers have interviewed cybercriminals who’ve used the face-altering technology to simulate someone else, and are also passing along stolen Personally Identifiable Information (PII) and deepfakes* as their own to apply for remote work positions
Read More
The Cybercrime Department of the Turkish National Police prepared a report available both in Turkish and English, aiming at contributing to the discussions of National 24/7 Points of Contact from other countries engaged in similar efforts and inspire academic discussions as well
Read More
Today, we witness large-scale cyber attacks that cause great damage to legal entities, access critical infrastructures and provide access to commercial or national secrets, and lock systems that prevent the fulfillment of legal entity activities. In the legal sense, if there is
Read More
Due to technological developments, cybercrime techniques evolve day by day. Nowadays, innocent users have been the target of cybercriminals whom want to make money or extort sexual favor in the context of sextortion crime. This paper discusses the definition of sextortion with
Read More
The study makes the legal definition of “corporate data” and refers to the methods of data prevent from theft attacks and security vulnerabilities. Link: https://www.academia.edu/40184081/Legal_Dimension_of_Corporate_Data_Security